Deploying AI
for business
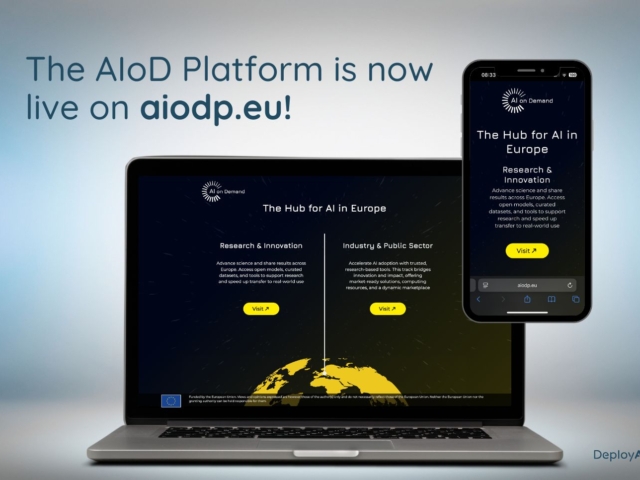
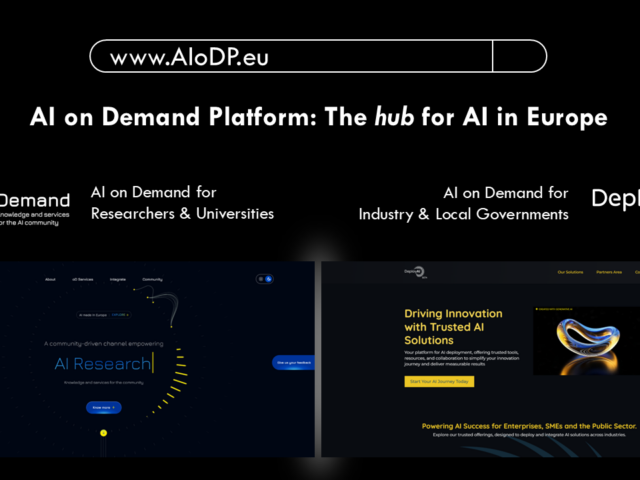
Explore the AI-on-Demand Platform
At DeployAI Project, we focus on providing start-ups, SMEs, and the public sector with access to European-standard AI infrastructure.
Our resource hub will offer a range of trustworthy, professional AI tools that seamlessly integrate into diverse projects and workflows.
Project Objectives
-
Scalable Platform
Develop a scalable AI platform with a marketplace for trustworthy AI resources and innovative services.
-
Integration
Integrate the AI platform into the European AI ecosystem, connecting with various infrastructures and stakeholders including AI Startups, SMEs and public administration.
-
Engagement
Create an effective engagement strategy for AI resource providers and users, boosting AI innovation in European AI Startups, SMEs and the public sector.
-
Sustainability
Establish a sustainable business model for the platform to ensure its growth and long-term success.
-
Enhancement
Enhance the platform with reliable AI resources, cutting-edge services, and practical use cases.